S3 Bucket
Overview
This service contains code to deploy an S3 bucket on AWS.
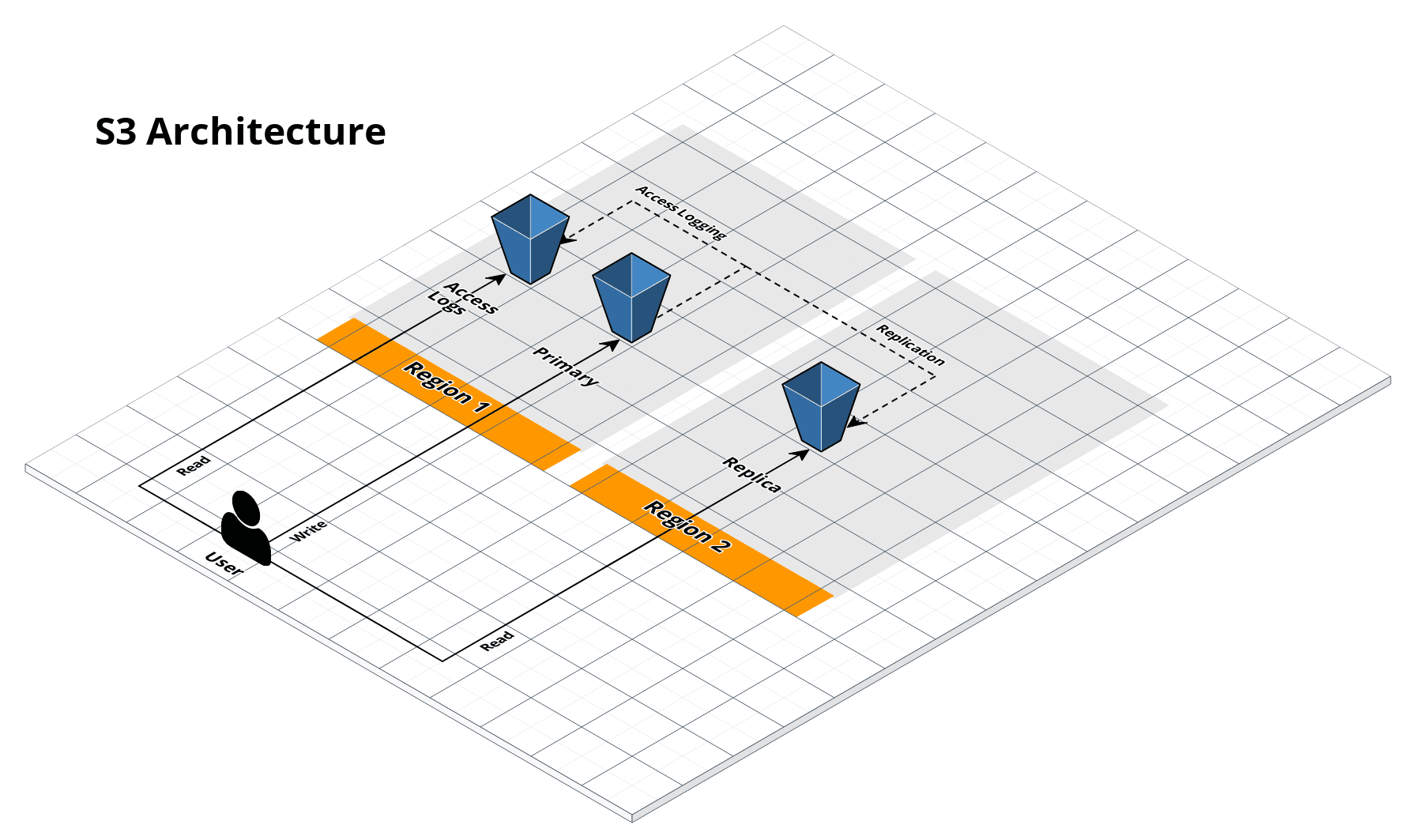 S3 bucket architecture
S3 bucket architecture
Features
- Deploy a private, secure S3 bucket
- Configure access logging to another S3 bucket
- Configure object versioning
- Configure cross-region replication
Learn
note
This repo is a part of the Gruntwork Service Catalog, a collection of reusable, battle-tested, production ready infrastructure code. If you’ve never used the Service Catalog before, make sure to read How to use the Gruntwork Service Catalog!
Gruntwork private-s3-bucket module: The underlying module that implements the private S3 bucket functionality.
S3 Documentation: Amazon’s docs for S3 that cover core concepts such as creating, accessing, copying and deleting buckets.
Deploy
Non-production deployment (quick start for learning)
If you just want to try this repo out for experimenting and learning, check out the following resources:
- examples/for-learning-and-testing folder: The
examples/for-learning-and-testingfolder contains standalone sample code optimized for learning, experimenting, and testing (but not direct production usage).
Production deployment
If you want to deploy this repo in production, check out the following resources:
examples/for-production folder: The
examples/for-productionfolder contains sample code optimized for direct usage in production. This is code from the Gruntwork Reference Architecture, and it shows you how we build an end-to-end, integrated tech stack on top of the Gruntwork Service Catalog.How to enable MFA Delete?: step-by-step guide on enabling MFA delete for your S3 buckets.
Reference
- Inputs
- Outputs
Required
primary_bucketstring(required)What to name the S3 bucket. Note that S3 bucket names must be globally unique across all AWS users!
Optional
access_logging_bucketstring(optional)The S3 bucket where access logs for this bucket should be stored. Set to null to disable access logging.
nullaccess_logging_bucket_lifecycle_rulesany(optional)The lifecycle rules for the access logs bucket. See lifecycle_rules for details.
{}access_logging_bucket_ownershipstring(optional)Configure who will be the default owner of objects uploaded to the access logs S3 bucket: must be one of BucketOwnerPreferred (the bucket owner owns objects), ObjectWriter (the writer of each object owns that object), or null (don't configure this feature). Note that this setting only takes effect if the object is uploaded with the bucket-owner-full-control canned ACL. See https://docs.aws.amazon.com/AmazonS3/latest/dev/about-object-ownership.html for more info.
nullaccess_logging_bucket_policy_statementsany(optional)The IAM policy to apply to the S3 bucket used to store access logs. You can use this to grant read/write access. This should be a map, where each key is a unique statement ID (SID), and each value is an object that contains the parameters defined in the comment above.
{}access_logging_prefixstring(optional)A prefix (i.e., folder path) to use for all access logs stored in access_logging_bucket. Only used if access_logging_bucket is specified.
nullbucket_kms_key_arnstring(optional)Optional KMS key to use for encrypting data in the S3 bucket. If null, data in S3 will be encrypted using the default aws/s3 key. If provided, the key policy of the provided key must allow whoever is writing to this bucket to use that key.
nullbucket_ownershipstring(optional)Configure who will be the default owner of objects uploaded to this S3 bucket: must be one of BucketOwnerPreferred (the bucket owner owns objects), ObjectWriter (the writer of each object owns that object), or null (don't configure this feature). Note that this setting only takes effect if the object is uploaded with the bucket-owner-full-control canned ACL. See https://docs.aws.amazon.com/AmazonS3/latest/dev/about-object-ownership.html for more info.
nullbucket_policy_statementsany(optional)The IAM policy to apply to this S3 bucket. You can use this to grant read/write access. This should be a map, where each key is a unique statement ID (SID), and each value is an object that contains the parameters defined in the comment above.
{}bucket_sse_algorithmstring(optional)The server-side encryption algorithm to use on the bucket. Valid values are AES256 and aws:kms. To disable server-side encryption, set enable_sse to false.
aws:kmscors_rulesany(optional)CORS rules to set on this S3 bucket
[]enable_ssebool(optional)Set to true to enable server-side encryption for this bucket. You can control the algorithm using sse_algorithm.
trueenable_versioningbool(optional)Set to true to enable versioning for this bucket. If enabled, instead of overriding objects, the S3 bucket will always create a new version of each object, so all the old values are retained.
trueforce_destroy_logsbool(optional)If set to true, when you run 'terraform destroy', delete all objects from the logs bucket so that the bucket can be destroyed without error. Warning: these objects are not recoverable so only use this if you're absolutely sure you want to permanently delete everything!
falseforce_destroy_primarybool(optional)If set to true, when you run 'terraform destroy', delete all objects from the primary bucket so that the bucket can be destroyed without error. Warning: these objects are not recoverable so only use this if you're absolutely sure you want to permanently delete everything!
falseforce_destroy_replicabool(optional)If set to true, when you run 'terraform destroy', delete all objects from the replica bucket so that the bucket can be destroyed without error. Warning: these objects are not recoverable so only use this if you're absolutely sure you want to permanently delete everything!
falselifecycle_rulesany(optional)The lifecycle rules for this S3 bucket. These can be used to change storage types or delete objects based on customizable rules. This should be a map, where each key is a unique ID for the lifecycle rule, and each value is an object that contains the parameters defined in the comment above.
{}mfa_deletebool(optional)Enable MFA delete for either 'Change the versioning state of your bucket' or 'Permanently delete an object version'. This cannot be used to toggle this setting but is available to allow managed buckets to reflect the state in AWS. Only used if enable_versioning is true. For instructions on how to enable MFA Delete, check out the README from the terraform-aws-security/private-s3-bucket module.
falsereplica_bucketstring(optional)The S3 bucket that will be the replica of this bucket. Set to null to disable replication.
nullreplica_bucket_already_existsbool(optional)If set to true, replica bucket will be expected to already exist.
falsereplica_bucket_lifecycle_rulesany(optional)The lifecycle rules for the replica bucket. See lifecycle_rules for details.
{}replica_bucket_ownershipstring(optional)Configure who will be the default owner of objects uploaded to the replica S3 bucket: must be one of BucketOwnerPreferred (the bucket owner owns objects), ObjectWriter (the writer of each object owns that object), or null (don't configure this feature). Note that this setting only takes effect if the object is uploaded with the bucket-owner-full-control canned ACL. See https://docs.aws.amazon.com/AmazonS3/latest/dev/about-object-ownership.html for more info.
nullreplica_bucket_policy_statementsany(optional)The IAM policy to apply to the replica S3 bucket. You can use this to grant read/write access. This should be a map, where each key is a unique statement ID (SID), and each value is an object that contains the parameters defined in the comment above.
{}replica_enable_ssebool(optional)Set to true to enable server-side encryption for the replica bucket. You can control the algorithm using replica_sse_algorithm.
truereplica_regionstring(optional)The AWS region for the replica bucket.
nullreplica_sse_algorithmstring(optional)The server-side encryption algorithm to use on the replica bucket. Valid values are AES256 and aws:kms. To disable server-side encryption, set replica_enable_sse to false.
aws:kmsreplication_rolestring(optional)The ARN of the IAM role for Amazon S3 to assume when replicating objects. Only used if replication_bucket is specified.
nullreplication_rulesany(optional)The rules for managing replication. Only used if replication_bucket is specified. This should be a map, where the key is a unique ID for each replication rule and the value is an object of the form explained in a comment above.
{}tagsmap(optional)A map of tags to apply to the S3 Bucket. These tags will also be applied to the access logging and replica buckets (if any). The key is the tag name and the value is the tag value.
map(string)
{}The name of the access logging S3 bucket.
The Route 53 Hosted Zone ID for this bucket's region.
The ARN of the S3 bucket.
The bucket domain name. Will be of format bucketname.s3.amazonaws.com.
The name of the primary S3 bucket.
The bucket region-specific domain name. The bucket domain name including the region name, please refer here for format. Note: The AWS CloudFront allows specifying S3 region-specific endpoint when creating S3 origin, it will prevent redirect issues from CloudFront to S3 Origin URL.
The name of the replica S3 bucket.